FreeRadius Server
Content
About
FreeRADIUS includes a RADIUS server, a BSD licensed client library, a PAM library, and an Apache module. In most cases, the word FreeRADIUS refers to the RADIUS server. FreeRADIUS is the most widely deployed RADIUS server in the world. It is the basis for multiple commercial offerings. It supplies the AAA needs of many Fortune-500 companies and Tier 1 ISPs. It is also widely used for Enterprise Wi-Fi and IEEE 802.1X network security, particularly in the academic community, including eduroam. The server is fast, feature-rich, modular, and scalable.
Version for Windows was dowloaded from http://www.freeradius.net/
Linux version according your Linux distribution (e.g. command "sudo apt-get install freeradius")
Version 3.0
Tested functions
| 2N IP Intercom | FreeRADIUS | TP-Link T1500G-10PS | MD5 Authentication | TLS Authentication |
|---|---|---|---|---|
2.27.0.36.6 | 3.0.16 |
2N IP Intercom Settings
Version 1.1.7
Tested functions
| 2N IP Intercom | FreeRADIUS | MD5 Authentication | |
|---|---|---|---|
2.13.0.22.1 | 1.1.7-r0.0.2 |
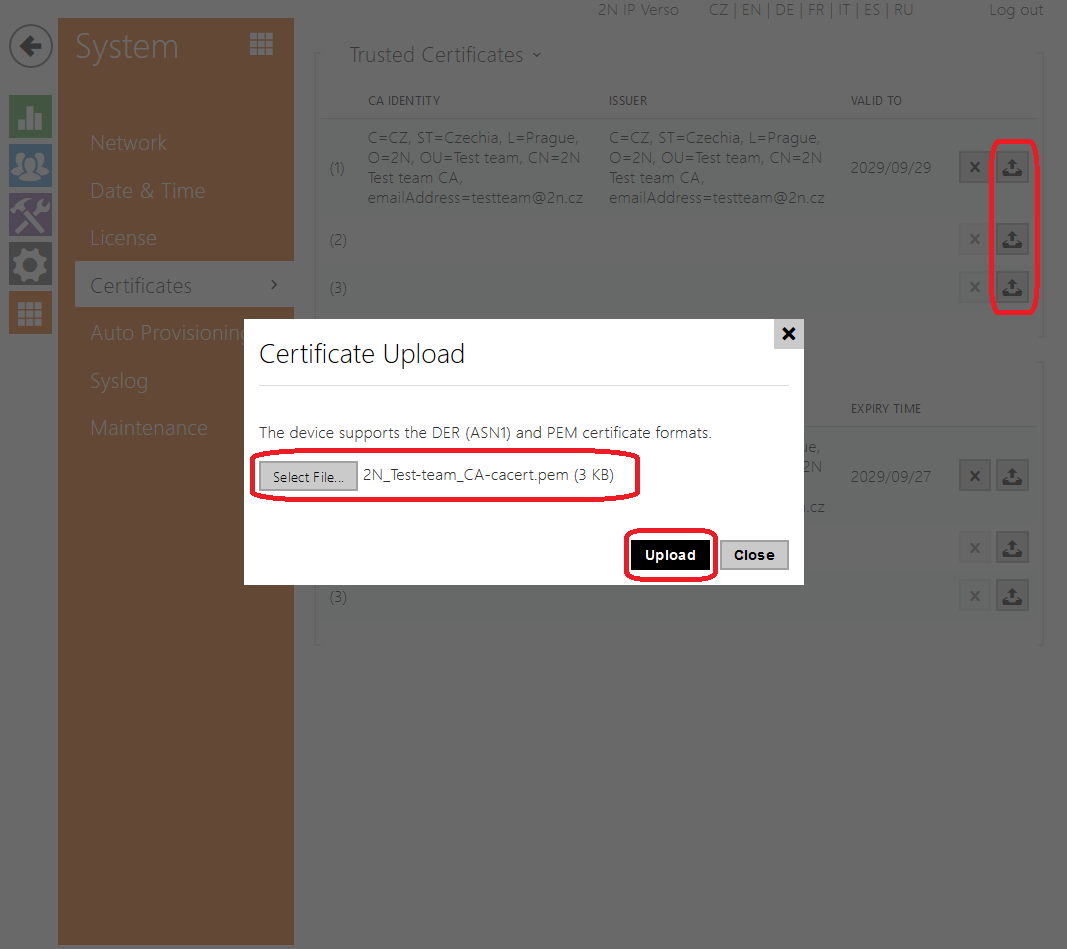
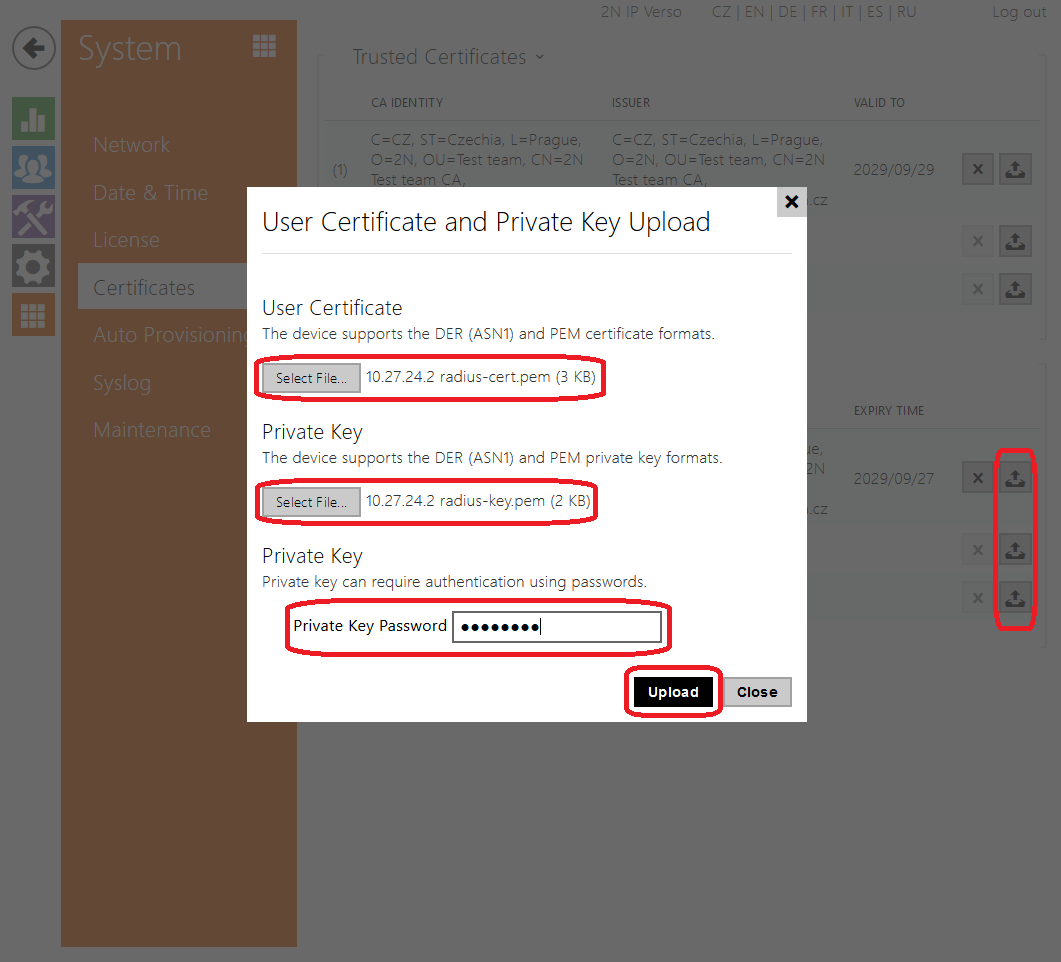
Configuration Guide
Used Symbols
- Compatible
- Work with limitation
- Incompatible